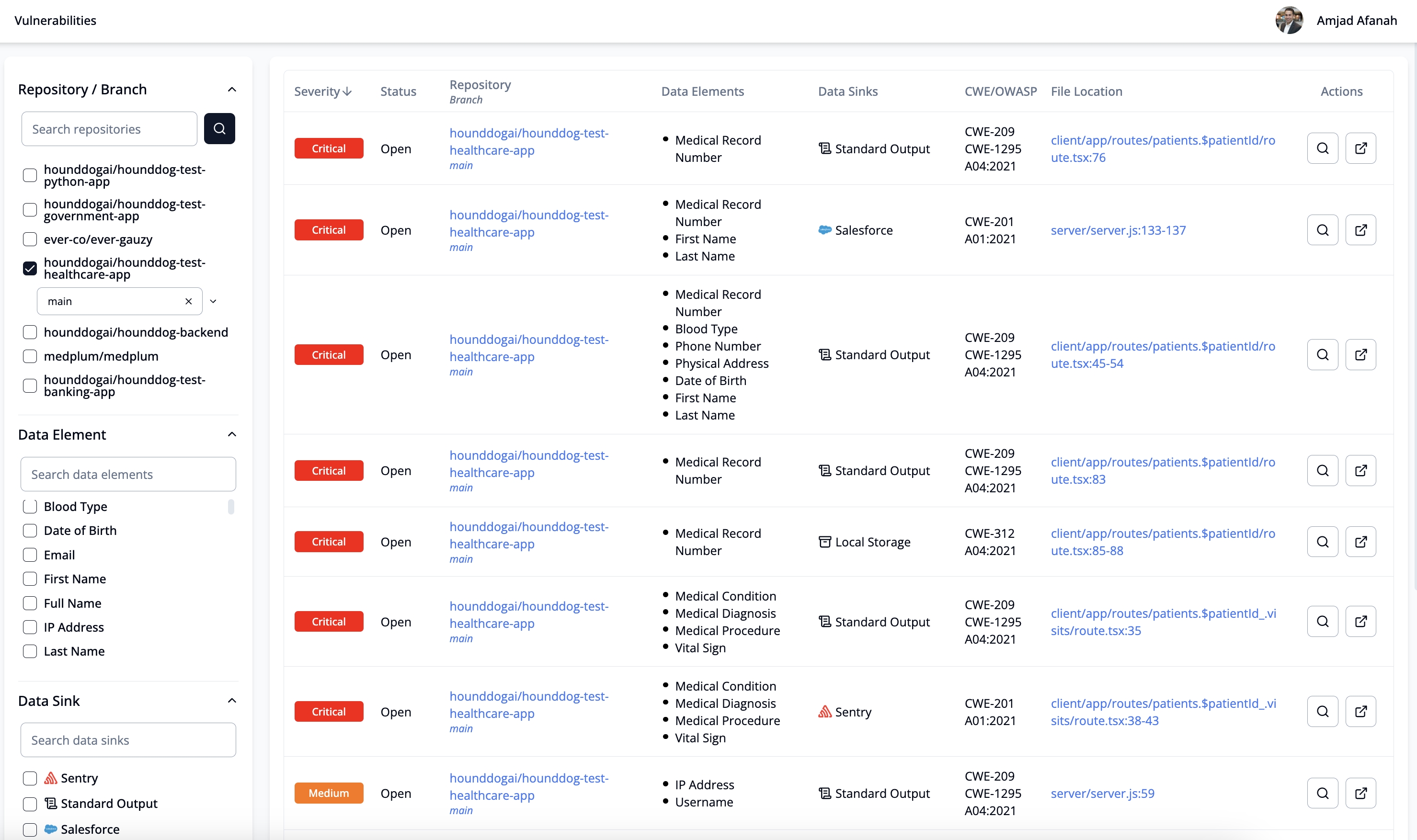
The vulnerabilities page allows you to view detected vulnerabilities using advanced filters covering:
- Repository
- Branch
- Data Elements
- Severity
- Status
You can then drill down into one of the vulnerabilities by simply clicking on the row containing the target vulnerability.
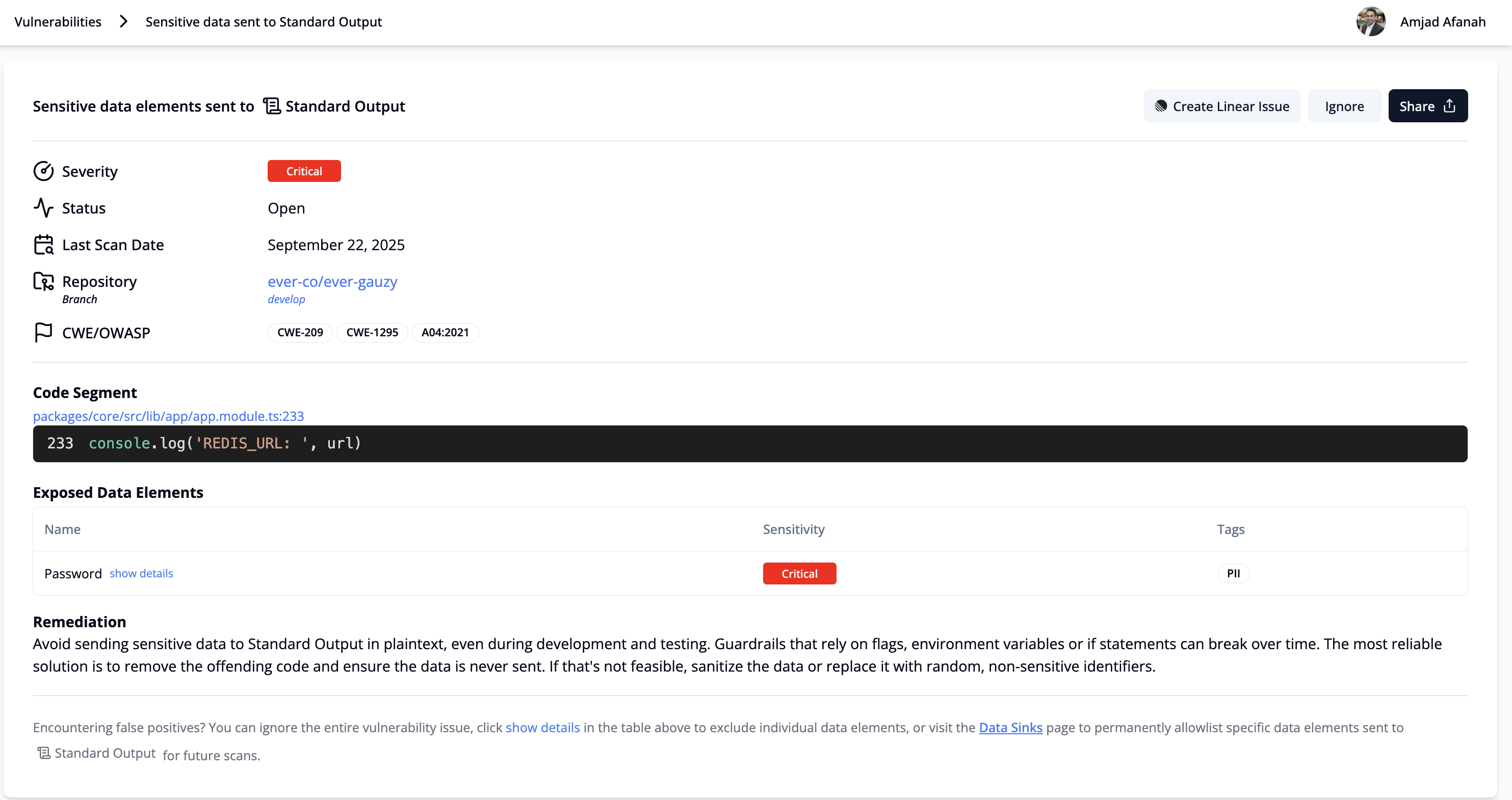
The vulnerability drill-down page allows you to view granular details about the vulnerability, including:
- Severity
- Status
- Last Scan Date
- Repository and Branch Details
- Relevant CWE and OWASP Categories
- Relevant Privacy Frameworks
- Storage Medium or Third-Party Integration Where Sensitive Data Is Exposed
- File URL
- Code Segment
- Remediation Guidelines
- Data Elements Detected
Lastly, there are three actions that can be taken on this page:
- File Jira or Linear Ticket: You will need to configure Jira or Linear on the Settings page to take advantage of this feature.
- Ignore this vulnerability: This will change the status from Open to Ignored.
- Ignore individual data elements: If a data element (e.g., username) is falsely flagged, you can ignore that specific data element, while the unignored ones will continue to appear. The severity of the issues will then be adjusted based on the sensitivity of the remaining unignored data elements.
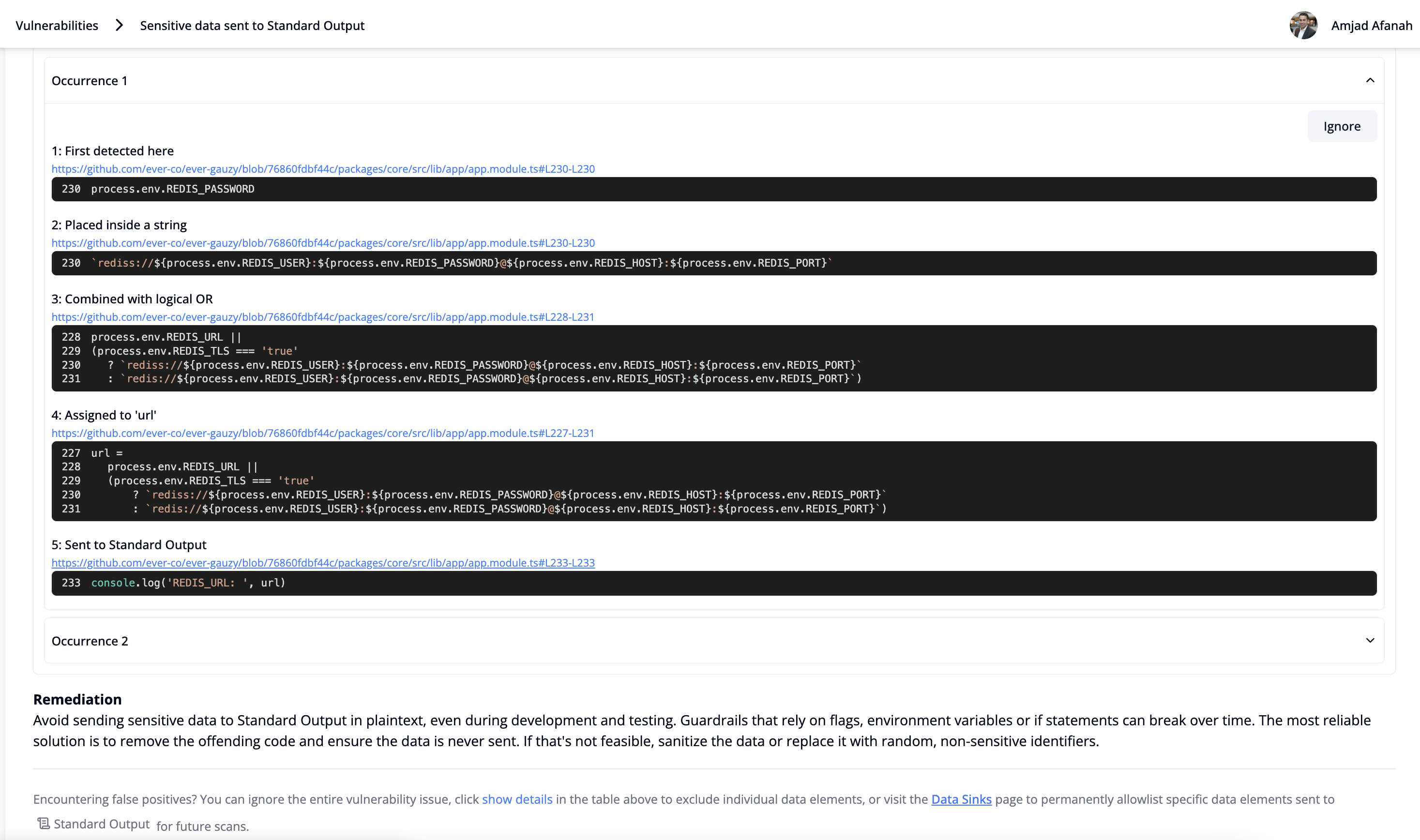
- View a detailed data flow trace: For each exposed data element, you can click "Show Details" to see a full trace of all transformations, including how tainted variables flow across files, that ultimately led to the sensitive data being exposed in the risky data sink.