Title
Create new category
Edit page index title
Edit category
Edit link
Overview
HoundDog.ai's Privacy by Design Code Scanner helps organizations proactively detect and prevent the overexposure of sensitive data in high risk mediums that could lead to privacy violations. The scanner embeds privacy into every stage of development, from IDE to CI. It discovers third party and AI integrations, including shadow AI, detects exposures of Personally Identifiable Information (PII), Protected Health Information (PHI), and authentication tokens in LLM prompts and other often overlooked surfaces such as logs, local storage, and third party SDKs, blocks unapproved data types before code reaches production, and generates audit ready RoPA, PIA and DPIA reports prefilled with detected data flows and privacy risks.
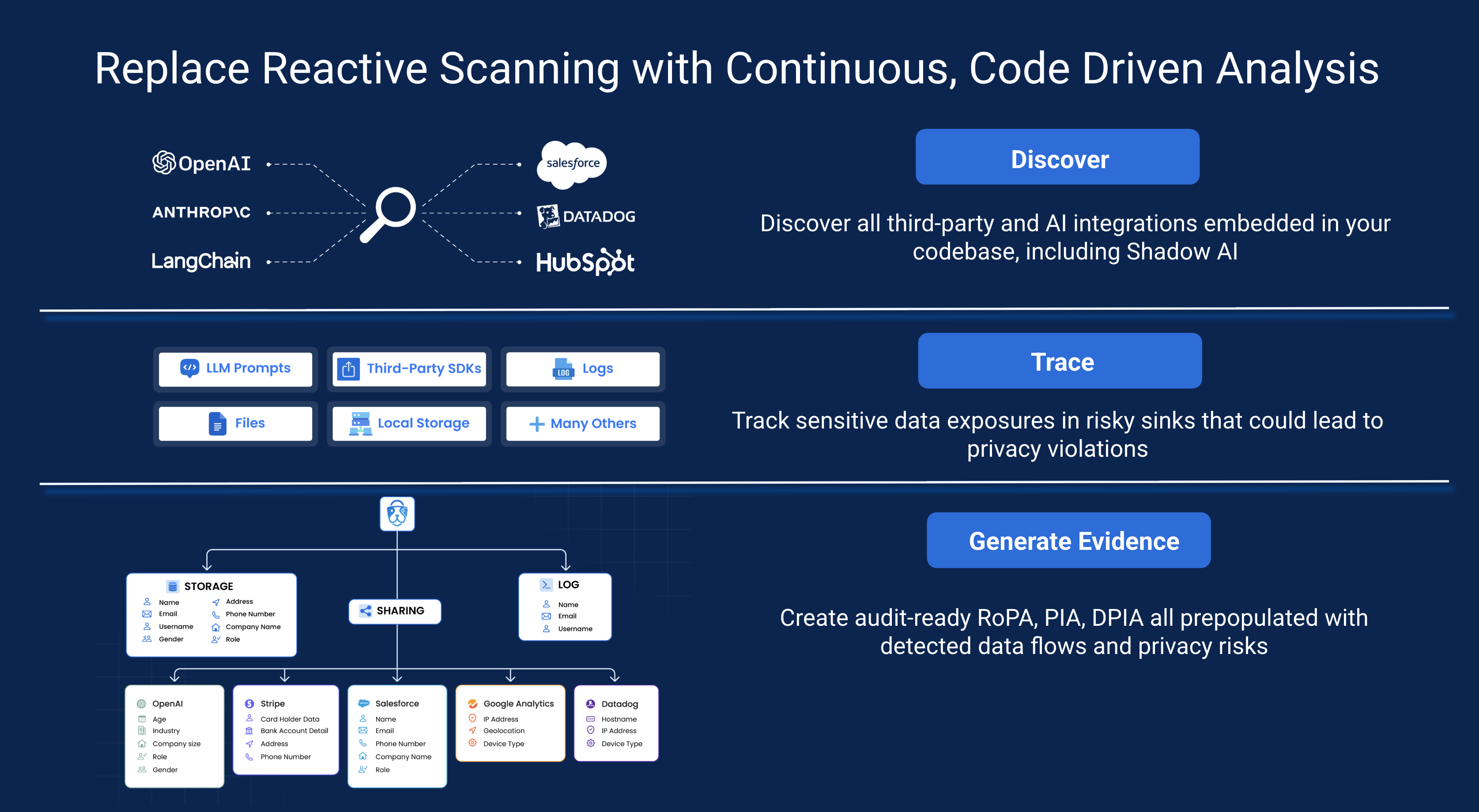
The platform enables organizations to:
🧭 Step 1: Discover AI and third-party integrations
- Track with high confidence the types of AI and third party integrations that developers have embedded in their code repositories as part of your AI governance and third party risk management efforts.

🔐 Step 2: Trace sensitive data flows
- Track over 100 sensitive data types, including PII, PHI, CHD and authentication tokens. Follow them through transformations such as tainted variables across file boundaries, no matter how deeply buried, down to risky sinks such as LLM prompts, logs, temporary files, local storage, and third-party SDKs.
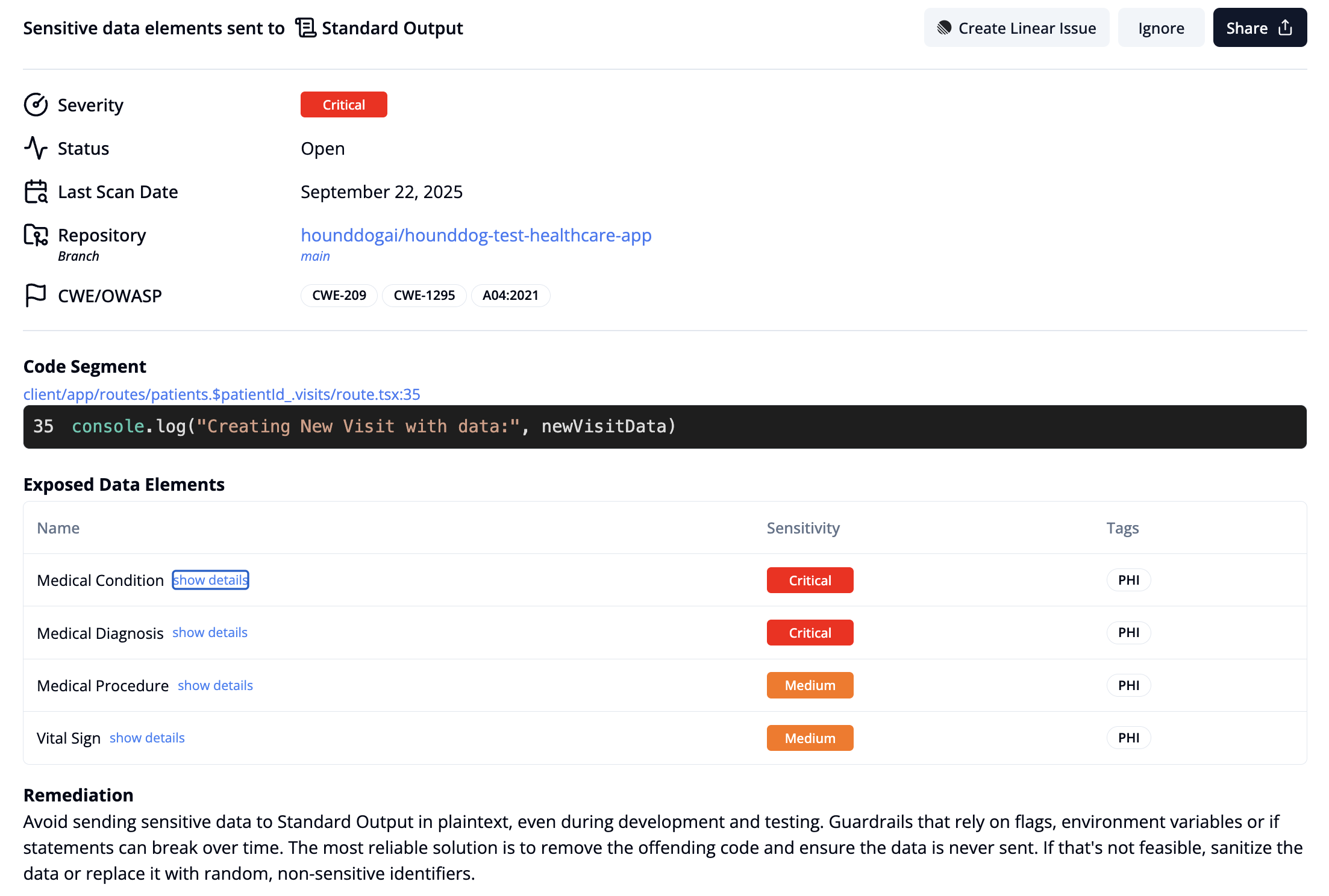
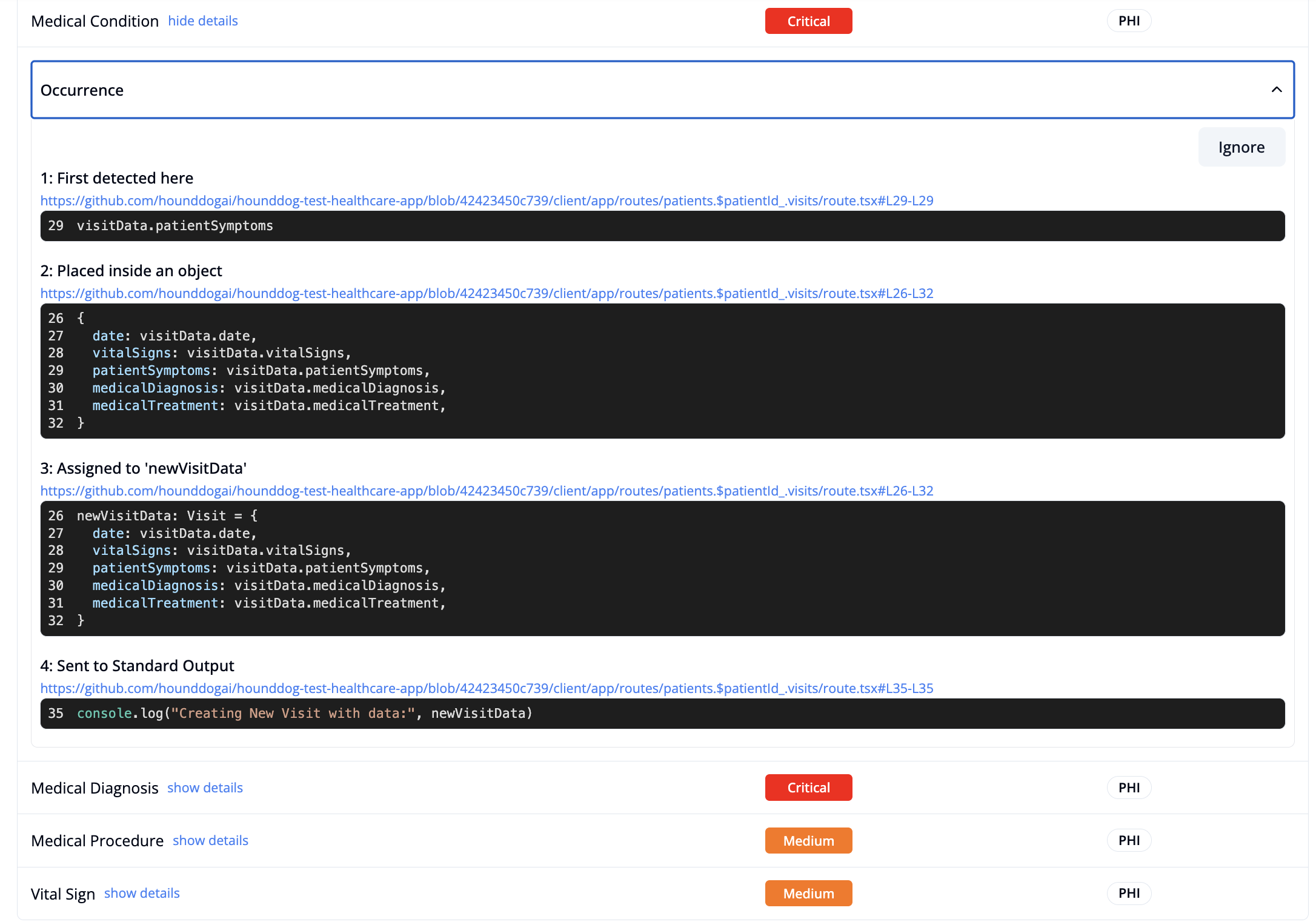
⚖️ Step 3: Bake in your privacy standards
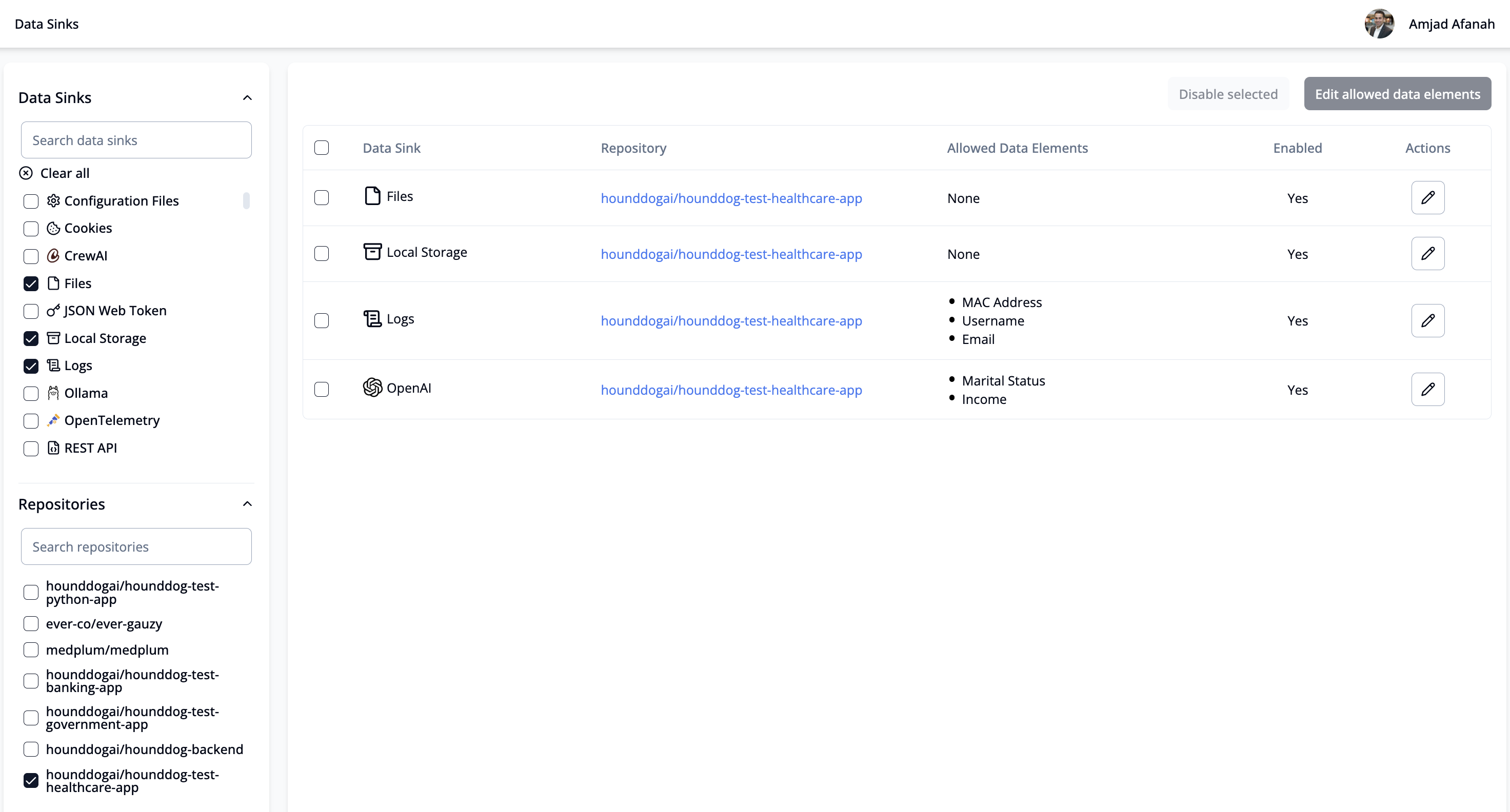
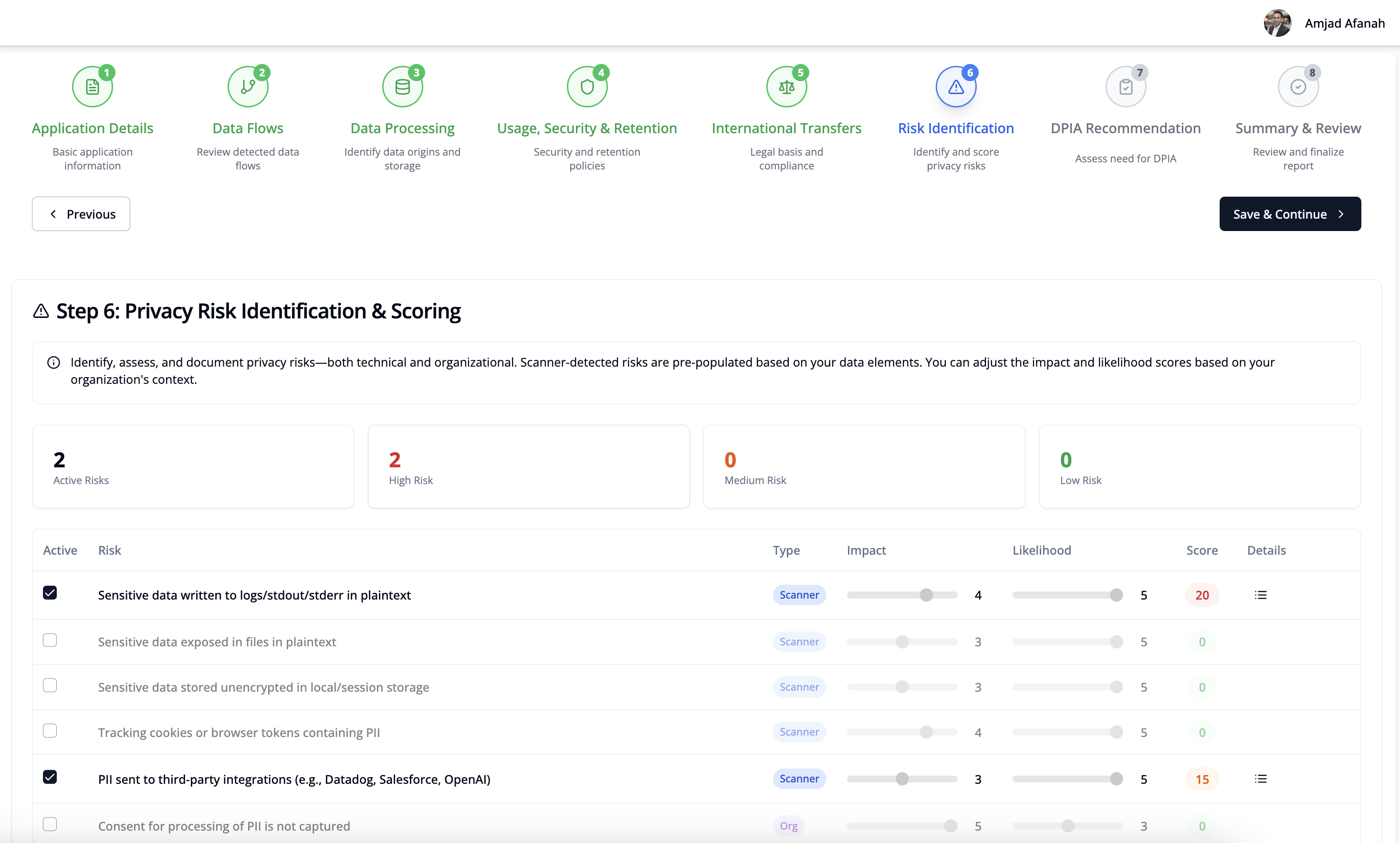
- Apply allowlists to define which data types are permitted in LLM prompts and other risky sinks. Automatically block unsafe pull requests to maintain compliance with Data Processing Agreements.
📑 Step 4: Build customer trust through transparent data handling
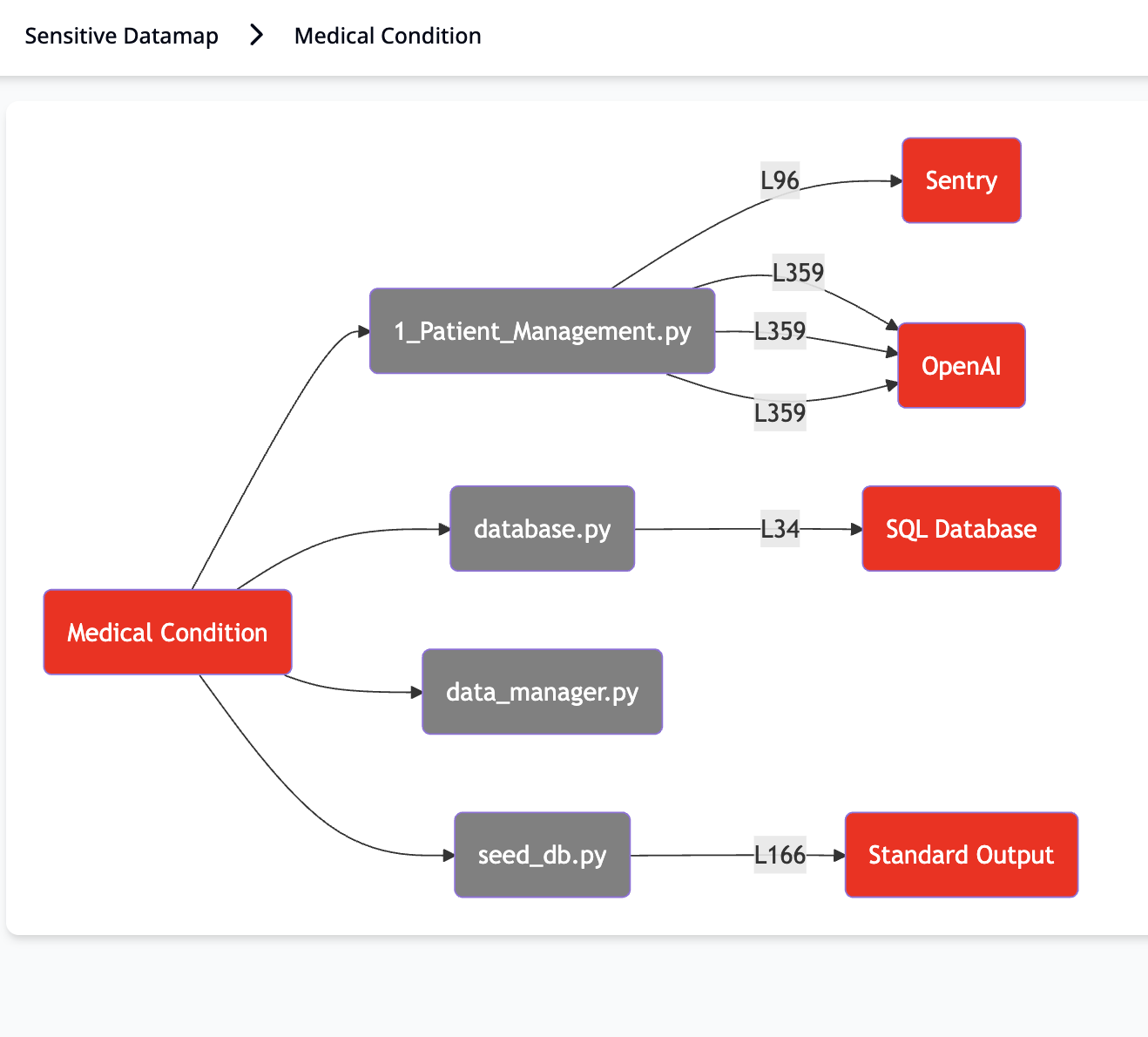
- Generate evidence-based data maps that show where sensitive data is collected, processed and shared, including through AI and third-party integrations.
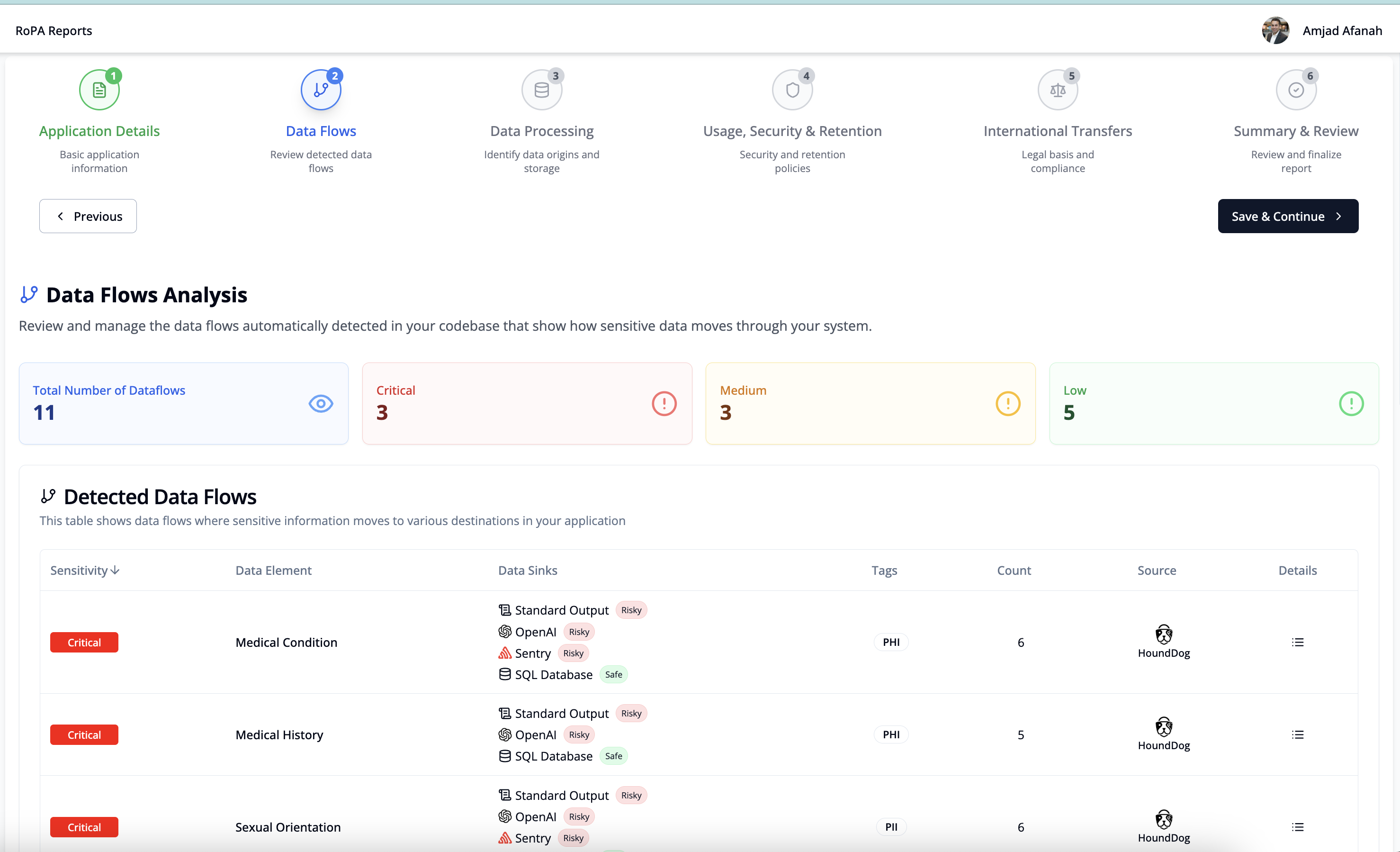
- Produce audit-ready Records of Processing Activities (RoPA) and Privacy Impact Assessments (PIAs), pre-populated with detected data flows and privacy risks aligned with GDPR, CCPA, HIPAA, and other regulatory frameworks.
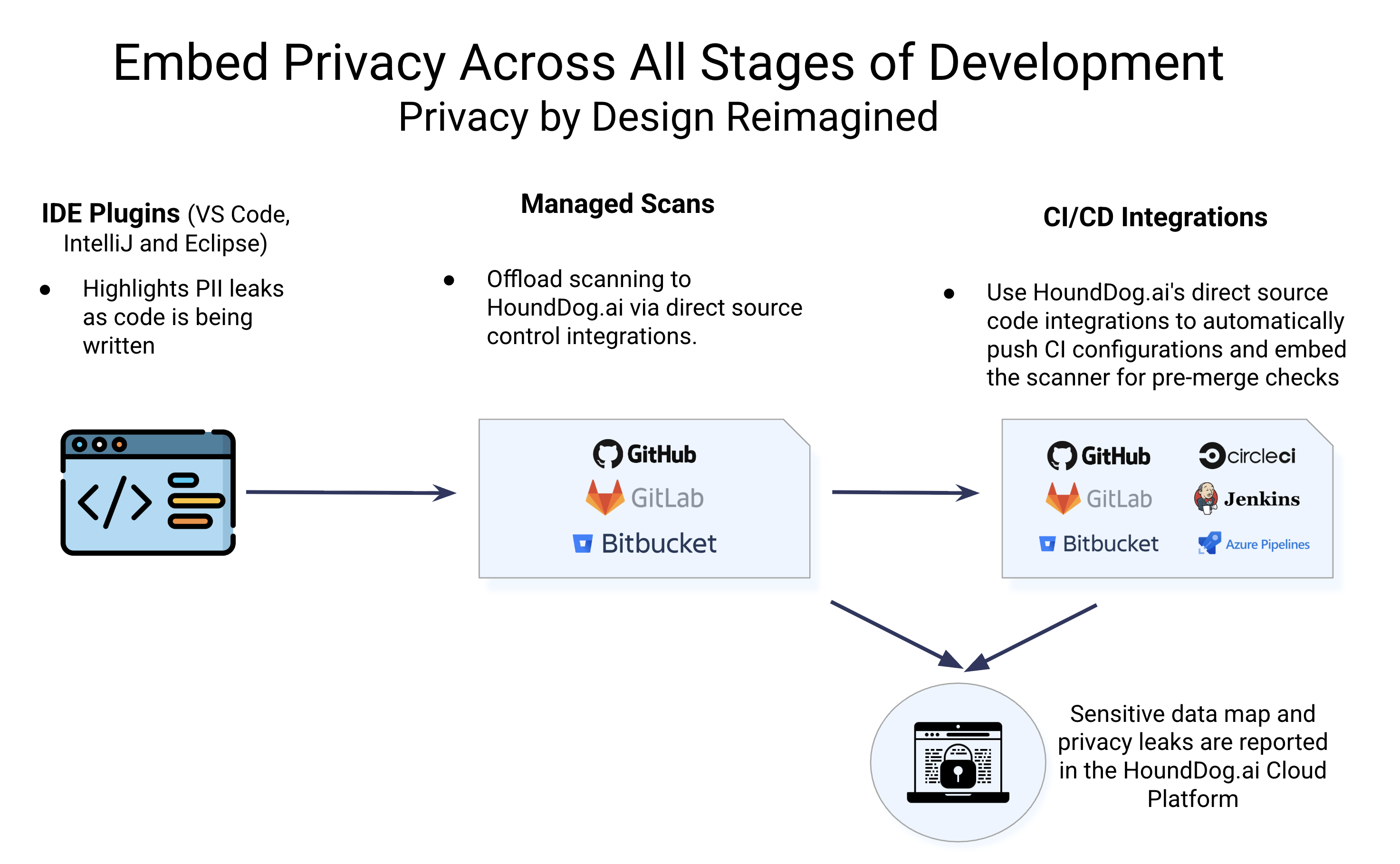
Embed Privacy Across All Stages of Development
HoundDog.ai's Privacy by Design Code Scanner can be used as a CLI that installs locally to scan cloned code repositories, or as IDE plugins that flag sensitive data leak issues as code is being written. The IDE plugins are available for VSCode, Cursor, JetBrains, and Eclipse. The HoundDog.ai Cloud Platform also provides Source Code Management Platform Integrations - connecting directly to GitHub, GitLab, and Bitbucket (both cloud and enterprise versions) to automatically scan code, block PRs, and leave actionable PR comments.
Free vs Paid Plans
For details on what is included in the free version and the paid plans, please visit our GitHub repository or pricing page for the most up to date information.
© 2025 HoundDog.ai, Inc. All rights reserved.