IDE Plugins
v1.0
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
IDE Plugins
Copy Markdown
Open in ChatGPT
Open in Claude
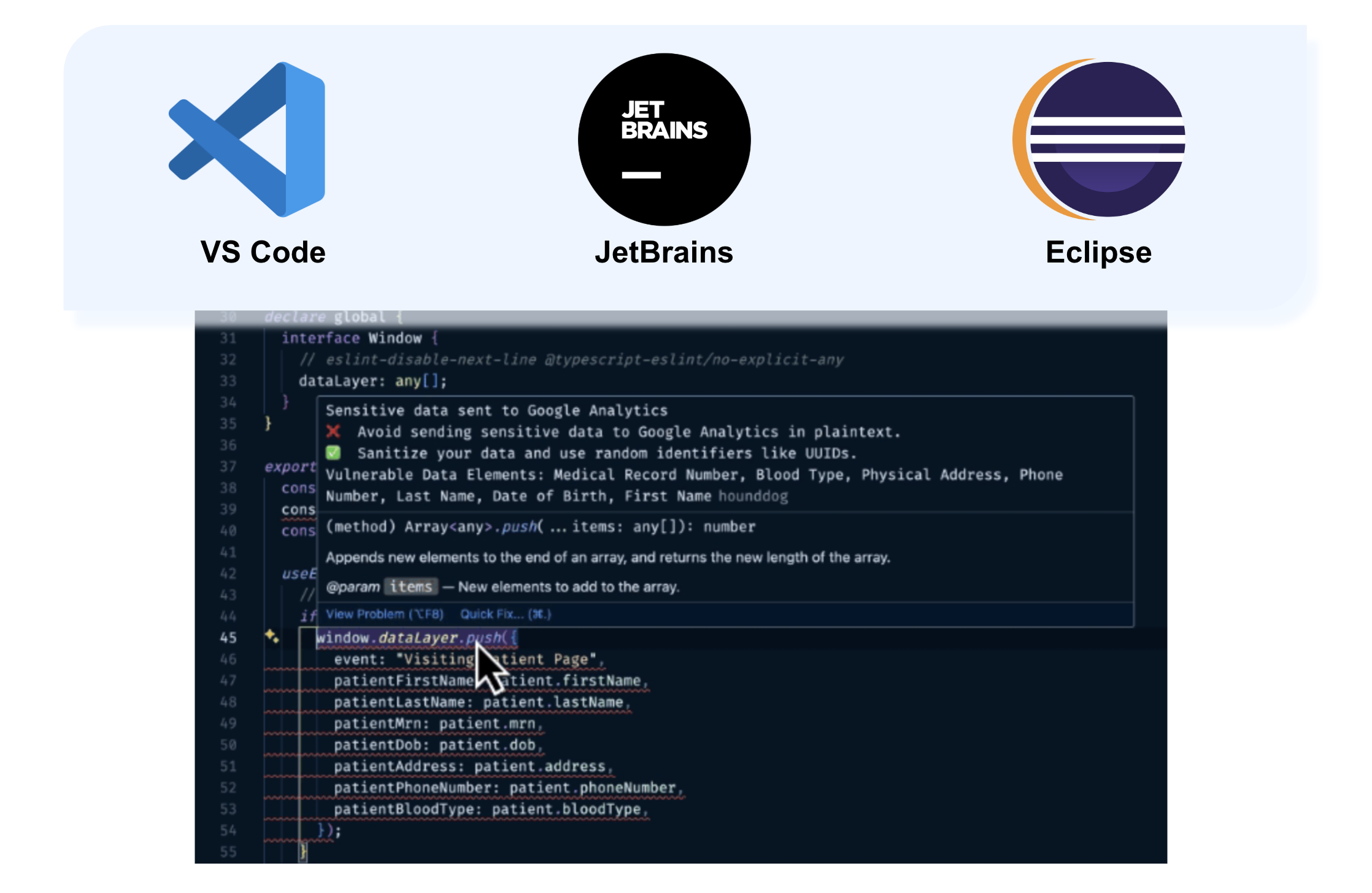
The plugins offer real-time code analysis within the IDE, identifying PII leak vulnerabilities. They provide remediation suggestions, which generally involve either removing sensitive data from logs, files, or third-party systems or applying standard data sanitization techniques, such as masking or encryption. The IDE plugins require an API key, which must be generated by the developer intending to use them.
Generate an API Key
- Developers can log in to app.hounddog.ai using Okta and navigate to the API Key section to generate a unique API key.
Install IDE Plugins
Follow the instructions in the respective IDE plugin marketplaces to install and configure the plugins:
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
© 2025 HoundDog.ai, Inc. All rights reserved.
Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message